RoutersThe routers are used to transmit the data packets between different networks. These are the hardware devices, which are placed at gateways of two connected networks. For example, if we want to connect our LAN to our ISP, we can use the router. Using the router, we can connect our network with the internet. 
Working of RoutersA router checks the IP address of the source and destination of each packet. After that, it will go to the routing table, which provides directions to transfer the data to the destination of a particular network and check the destination of the packet. Then it will route the packet to another router. This process will stop when the destination IP is reached and responded back. If we have many ways to go to the IP address of the destination, the router will select the most economical way. If the list of routing table does not contain the packet's destination IP address, the default router will get the packet. If the packet has no destination, the packet will be dropped. 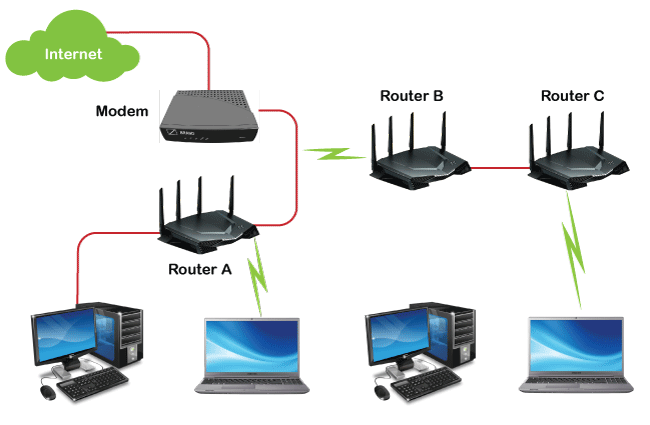
Most routers have different ports so that they can connect the different devices to the internet simultaneously. The router uses the routing table to find out where the traffic is coming and where to send the data. Generally, ISP (Internet service provider) provides the router. The ISP assigns our router's IP address, and that IP address is the public IP address. Whenever we use the internet on our device, we are identified in the world using the public IP address. Routers keep our private IP addresses protected. Our laptop, TV media box, desktop, and network copier have different private IP addresses. If they don't have a different private IP address, the router will be unable to recognize the requesting device. Importance of RouterThe following are some importance of router:
Security features of RoutersThe following are some security feature of the router:
FirewallIn the event of an emergency, the firewall is used as a wall to block the fires. A network firewall is used to set a barrier between the internet and LAN (local area network). The purpose of a network firewall is to protect our private LAN. It is used to save our important data from leaking out. Without the firewall capability, the routers will blindly pass traffic between two different networks. A firewall is used to monitor the traffic and block the traffic, which is not authorized to go out. A network firewall separates the internet and the LAN. In the LAN, it also segments the ordinary data and the important data. Due to this, the internal invasion can be avoided. You will determine the amount of threats that are blocked by your firewall. By blocking, firewall prevents your private network from outside users. You need to create a Demilitarized Zone (DMZ) if you allow remote access from others to your network. Most of the firewall provided the DMZ option. It will designate a directory on the computer of a gateway, just like Demilitarized Zone. Virus protected is offered by some firewalls. It is recommended for every computer to install the anti-virus. 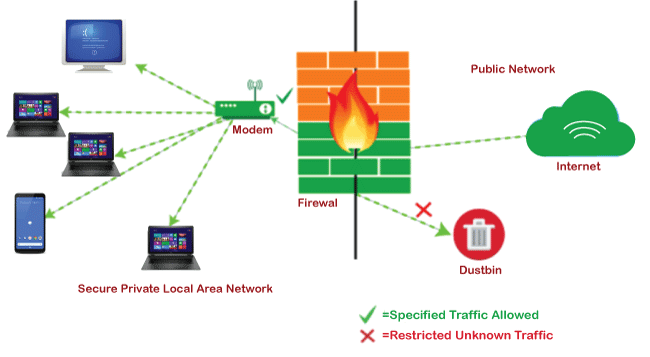
Working of Network FirewallSome hardware firewalls allow you to define the blocking rules like UDP (User diagram protocol) or TCP (transmission control protocol) or by IP address. This helps you to forbidden the IP address and unwanted ports. Software applications and services define some other type of firewall. Such firewall acts like a proxy server, which is used to interconnect the two separate networks. The combination of a software firewall and a hardware firewall is more efficient and safer. Importance of Firewall
Security features of the firewall
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










