Subdomain DiscoveryPublic resources for subdomain discoveryWe can cache the information of the subdomain using the various available public resources. In order to perform the specific purpose, some of these websites are created. Another website, like a search engine, is used to index the public resources, which is their main purpose. Using Google docs, it will become easy to siphoning a subdomain from Google. On the basis of only our target, the result will be filtered by the site directives: 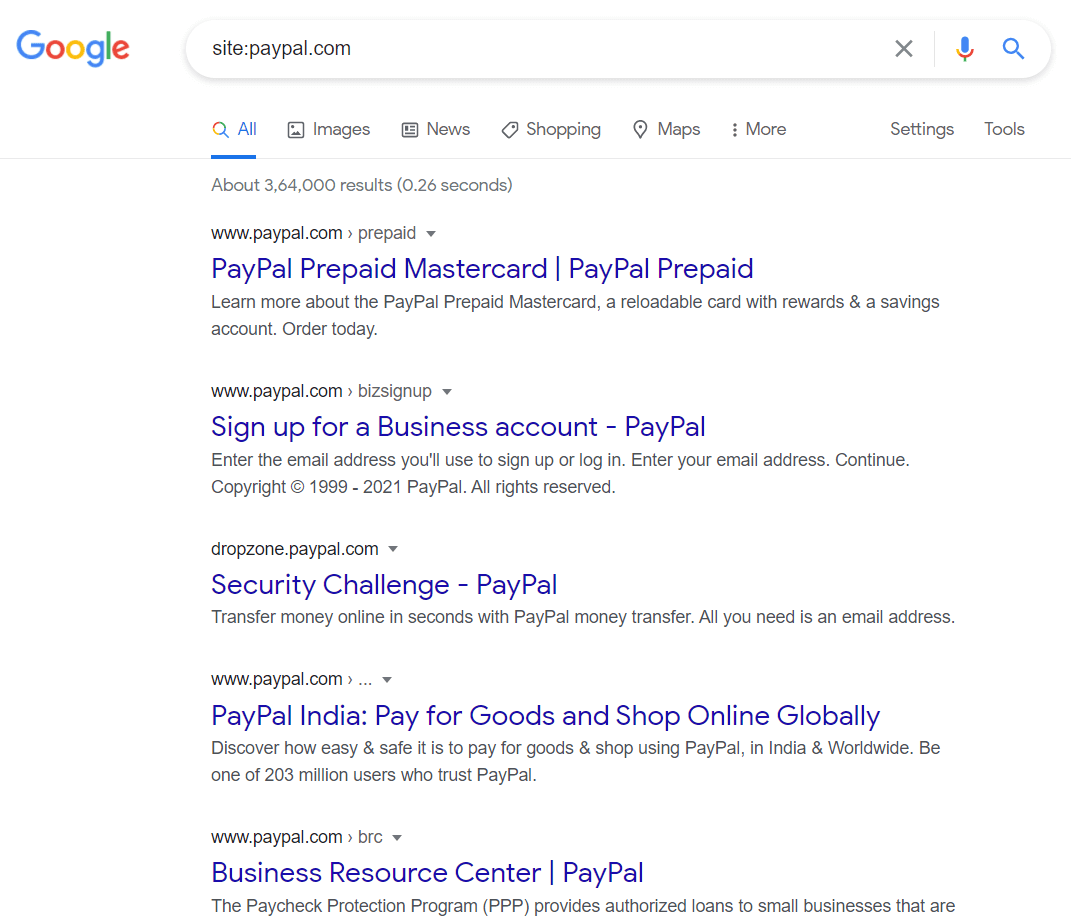
-inurl directives will be used when we have the initial domain. Using the -inurl directives, we can filter the subdomain which we find so that we can provide more place for others: 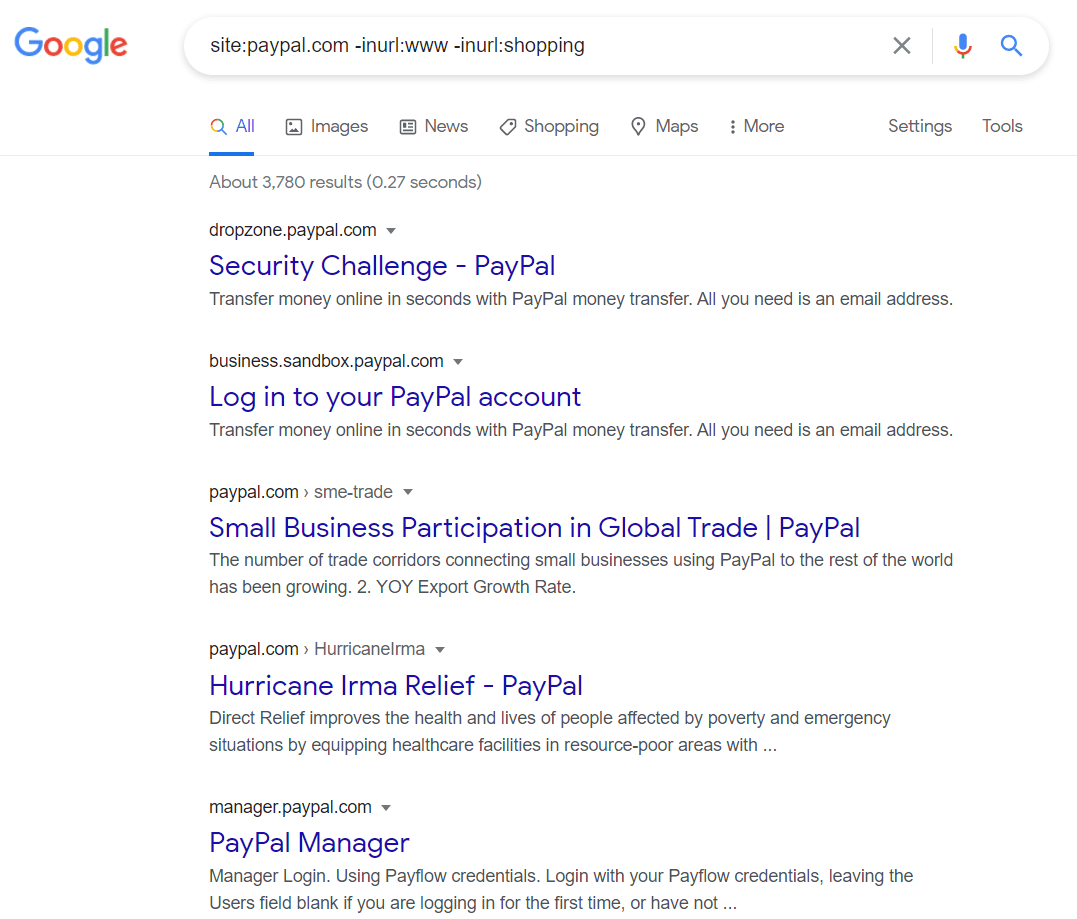
When all the possibilities are noting and iterating, and our search gets no more results, we get the subdomain's great starting point. If we do this manually, it will create pain for us. But we have various tools that are used to automate this, and it can query more than one search engine at a time. Finding SubdomainIt will take an eternity if we are trying to find the subdomain manually. But fortunately, to do this, we have various subdomain scanning tools. The tasks of our daily subdomain reconnaissance can get effective using the following 7 subdomain scanning tools. In any company, the full domain infrastructure can be explored by the subdomain scanner utilities in the world. The toolkits of these subdomain enumerations have various uses, but the most popular usage of these is as following: DNS AuditEvery week the news related to DNS attack run media. It is odd, but most of the companies never perform a scheduled DNS audit. The most effective way to determine expired SSL certificates, unused subdomains, exposed legacy software, find and update records of stale DNS is by running a DNS audit. Our application and system can be hardened using this information. The information can also be used to update the document of our network infrastructure and our server. Domain IntelligenceSubdomain discovery is often used by the red terms in their infosec investigations. A number of OSINT techniques frequently involves in this investigation. The forgotten public areas are discovered by the subdomain enumeration tools, which will be used to exposing sensitive information related to our technologies, users or apps. Vulnerability scanningIf we want to find about any online company, the extensive list of a sub domain with their domain name will yield remarkable. When we audit the full list of a domain name with its subdomain, we can often find the development versions, private areas, and unprotected applications. After that, based on the common known vulnerabilities, we can massively scan these areas. Working of Subdomain scannerWe will then analyze subdomain scanners, which are the most popular methods, and we will find the subdomains using the domain tools. Querying search enginesWe can determine any domain name's subdomain using the Google hacking techniques. to do this, we can use a command, which is as follows: The Google indexed subdomain's list is returned by the above command. The latest GoogleBot crawl provides this subdomain query that's why it is not in real-time. This query is also used to determine all subdomains that do not use meta tags with noindex or are not protected by robots.txt configurations. This build-in query language relies on the subdomain scanner engine based on the web and many terminals from the search engine like Bing, Google, etc. Performing brute force discoveryIn order to generate the lists of a subdomain, recursive brute force and brute force techniques are used by some discovery tools. Mostly these lists are a combination of word-lists. Now we will test which subdomain is alive using a bunch of words. Probably this way does not seem like the quickest way to determine the subdomain, but we can say that it is the most accurate way among many ways. This type of method is used by many tools, and those tools include DNScan, Fierce, and Amass. Running DNS zone transfers.If we want to replicate the zone of remote DNS, another way to do this is DNS zone transfer. In the DNS server, all configured subdomains are revealed by the DNS zone transfer. When the system administrator limits the DNS zone for AXFR requests or not protected the DNS zone, this technique will only work. This DNS request type is patched by most DNS servers. We can make it worth it by combining it with exploration, which is based on brute force. Fetching SSL/TLS public informationIf we want to encrypt the data which is sent and received between browser and servers, SSL/TLS certificates will be very useful. In order to do the infosec research, SSL/TLS certificates can also use. We can extract subdomain and domain name by using the SAN of the SSL/TLS certificate. We can easily and quickly find this subdomain by the combination of python or bash scripting or this method.
Next TopicSubdomain scanner tools
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










