How to Secure Our Kali Linux to Ensure Our ProtectionKali Linux is an open-source Debian-based Linux distribution that is broadly used for offensive security. This Linux distribution, formerly known as Backtrack Linux, is a sign of security. Penetration testers across the world utilize Kali Linux. Cybersecurity students use it to practice penetration testing and other tasks. Running Kali Linux with the default settings, on the other hand, might be a bad decision, and the reason behind that is default settings are easy to crack, and Kali Linux is not privacy-focused distribution such as Tails OS; it is designed for attacking rather than defend. The concept of security is vast. The majority of people use Kali to test security, but it's equally critical to keep Kali safe. We have high security because it is built on Debian. But what if we require more protection? In this tutorial, we will learn how to make our Kali Linux system more secure. It's not a good idea to run Kali Linux with the default settings. Updating Kali Linux FrequentlyKali Linux comes in a variety of flavors. Every quarter, Kali Developers releases a new version. Kali's kernels have been upgraded to newer versions. Kali Linux does not require downloading an ISO image and installing it again during updates because it is a rolling distribution. In order to install the update, we only need to run a few commands. We have to use the following command in order to update Kali Linux: 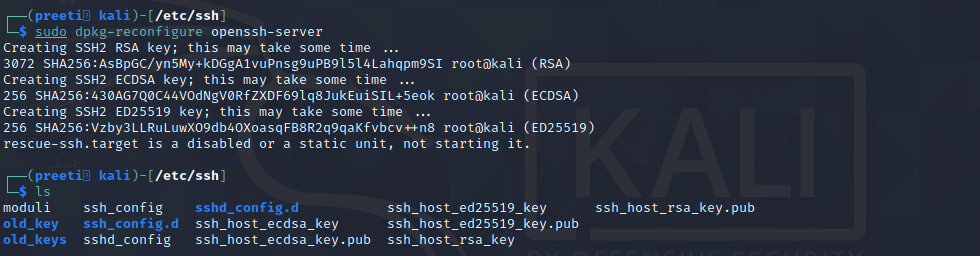
The conclusion is that we must routinely update and upgrade Kali Linux, and update the distribution whenever it is released. Save our IdentityDuring surfing the internet with a Kali Linux machine, we can use the "NIPE" or "Kalitorify" tools to browse safely and anonymously. Despite the fact that using "macchanger" to spoof our Mac address. We also recommend changing kali's hostname to the nameserver and adding a host like 8.8.8.8. Change the Default PasswordIf we are utilizing an older version of Kali Linux (older than 2020.1) then our default credential is "root" "toor". On the other hand, if we use newer Kali Linux versions, the default credential is "Kali" "Kali". We need to make a modification as soon as possible. It's simple. All we need to do is run the following command on our Kali Linux terminal: This simple command will prompt us for the user's current password (which will be default if we have not changed it yet). It will then prompt for a new password and verify it once more. A strong password must include uppercase and lowercase letters, as well as symbols and numbers. Our password will be changed after we have verified it. This can be seen in the screenshot below: 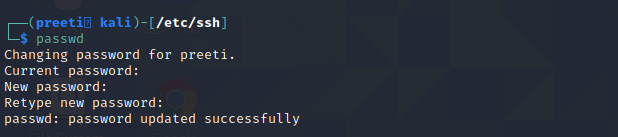
For security reasons, we must remember one thing that is our typed password will not be displayed. Unprivileged User AccountKali's default user was formerly root. After the Kali Linux 2020.1 things, have changed. The non-root user account is now Kali's default user. An unprivileged user stands directly below the main admin user, who has full root access. In the same way as family and parental accounts. We can also utilize a root directly on our system directly, but this is not recommended for security reasons. We should not constantly use the root user. Monitoring LogsExamining the logcheck program can be a real-life saver. It can send logged messages to the administrator's email address. By default, log files are saved locally in "/var/log." 
With the help of the top (built right into the system) or htop (sudo apt install htop) tools, we can see real-time monitoring activity. A similar task can be performed with the xfce4-taskmanager graphical tool. 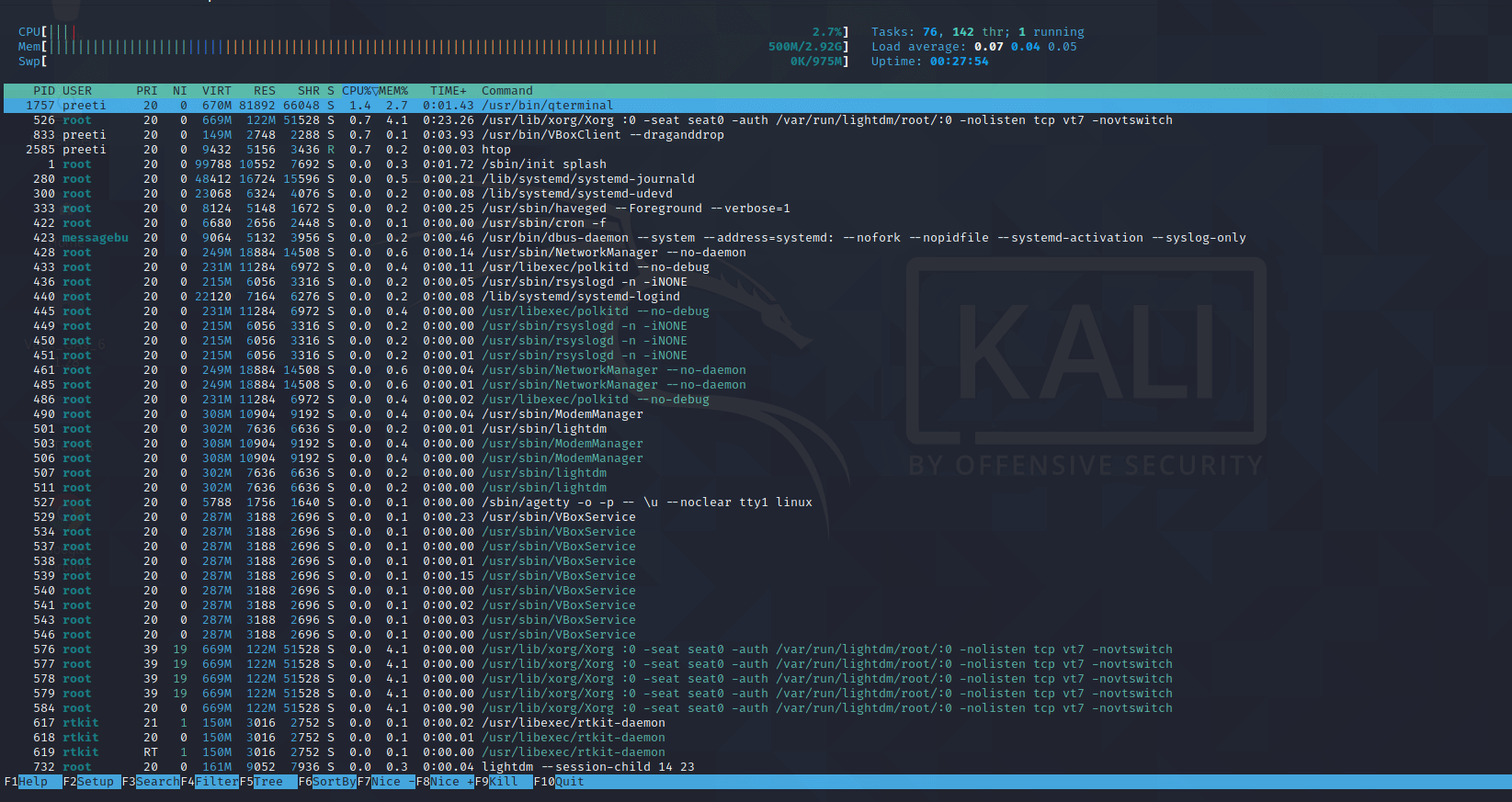
Scanning for Malware and Rootkits. We also need to check our system for malware and rootkits on a regular basis. The scan can be performed with the help of the "Chkrootkit" or "Rkhunter" tool kits. These tools are like anti-malwares for Linux systems. Changing the Default SSH KeysSSH, or Secure Shell, is a network protocol. It is used to securely communicate between computers. We are already utilizing SSH because we are on the page via the web. There are no other options than to address current or future security risks. SSH keys are available for all the distros we use, allowing us to verify the authenticity of files from a source. Everything may appear good and wonderful, but the problem is that everyone has the same keys. Let's take a look at this way. If we download a software from the website, it is a similar distribution copy that everyone downloads. After that, we utilize our accounts with the software in a personalized way, and the service provider provides sufficient power based on the subscription under those accounts. The principles of SSH keys are the same, except they are used to verify files. If a bad person did a Man-in-the-Middle (MITM) attack or a social engineering campaign, it may drain our security. SSH allows us to authenticate without having to type passwords every time. SSH keys are divided into two categories. One is public, and another one is private. We will need to alter our public SSH keys because they are the same across all distributions, and we will need to generate a private key to ensure that only authenticated users can access it. By default, SSH keys are stored in the /etc/ssh/ directory. This list view displays all of the keys inside. We will save them somewhere else rather than deleting them from the database. To do so, we use the following commands: All of our old SSH keys have now been transferred to a directory called old key. 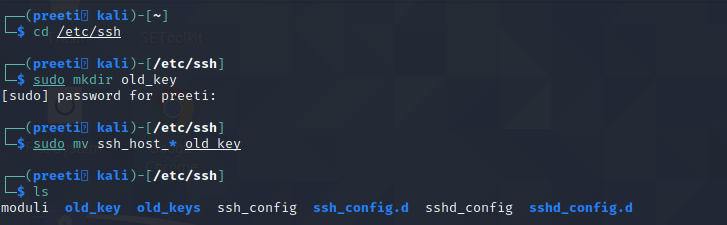
Using the following command, we can now generate new keys: For us, this command will generate a new SSH key. As we can see in the below screenshot: 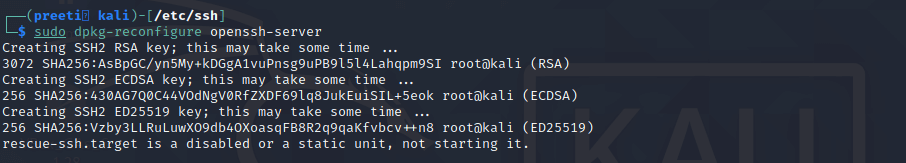
We can utilize our backup SSH keys if we have any problems. |
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










